Cybersecurity for Smart Factories:
A 2025 Playbook for OT Resilience

Why “smart” now means “secure” or not at all
Smart factories are powered by data, sensors, and highly-coupled supply chains, beneficial for OEE, disastrous if an attacker gains a foothold. In the last year, UK authorities reported a 50% increase in nationally significant cyber attacks, emphasizing that this is now a board-level risk, not “just IT.”
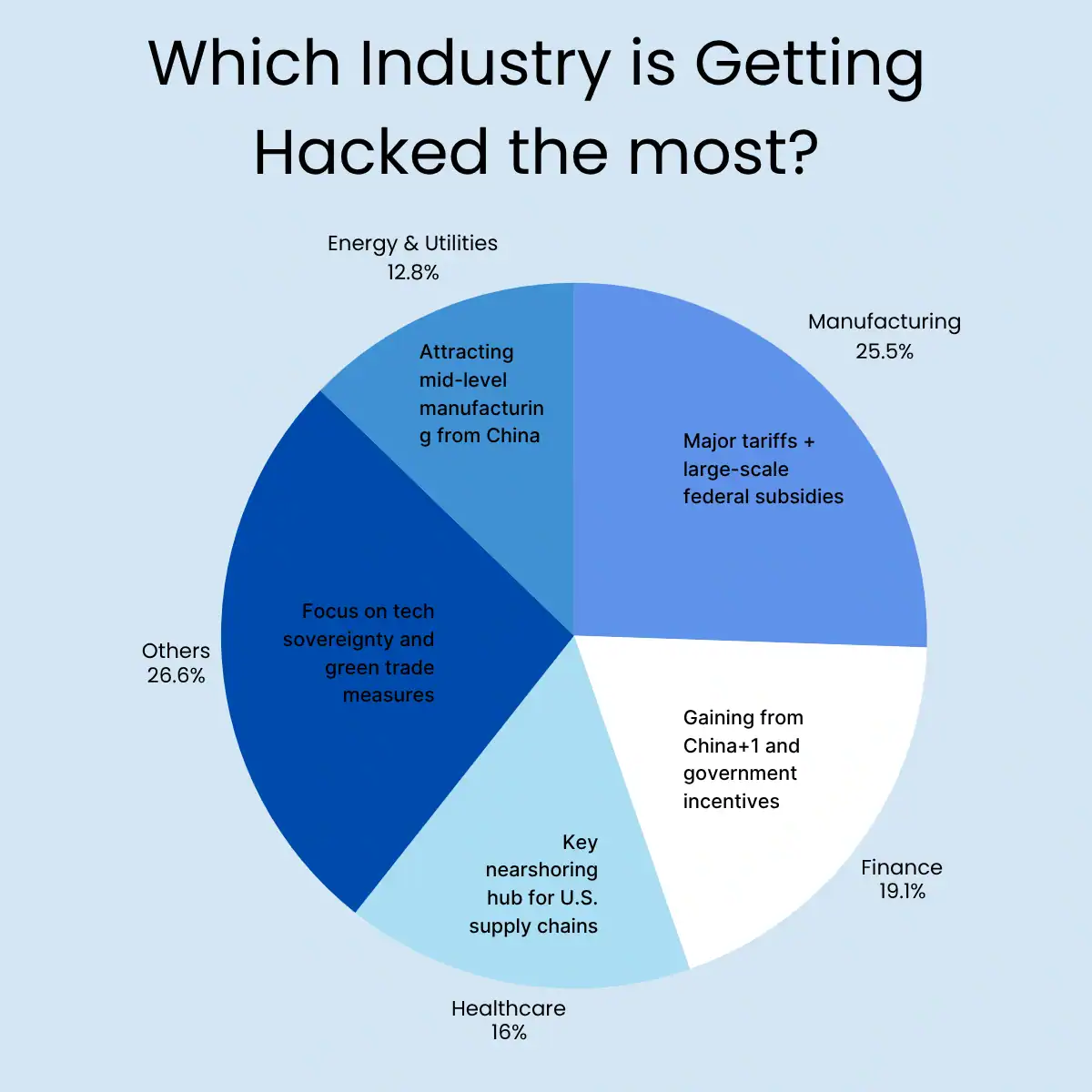
If you make things, the odds are against you: various industry reports illustrate that manufacturing is the most-targeted industry globally—a fertile mix of legacy OT, 24/7 uptime pressure, and expansive vendor networks.
Smart factories are only as smart as their operational technology (OT) security.
Manufacturing remains the most targeted industry for the fourth consecutive year… accounting for 26% of incidents
The threat landscape in 60 seconds
Ransomware was never dead, it changed modes. Encryption-only attacks fell off, yet data theft and extortion rose, putting lines in danger even without complete lock-outs.
Packetlabs
Availability is supreme. ENISA’s latest landscape lists availability/ransomware/data attacks as the leading trio of threats exactly what factories despise most.
Adversaries love “what’s exposed.” Public-facing apps and remote access are favorite entry points before pivoting into OT.
Regulators are baring teeth. The EU and UK are pushing faster incident reporting and stronger supply-chain demands.
What good looks like: Usable standards
If you learn just two acronyms, make them these:
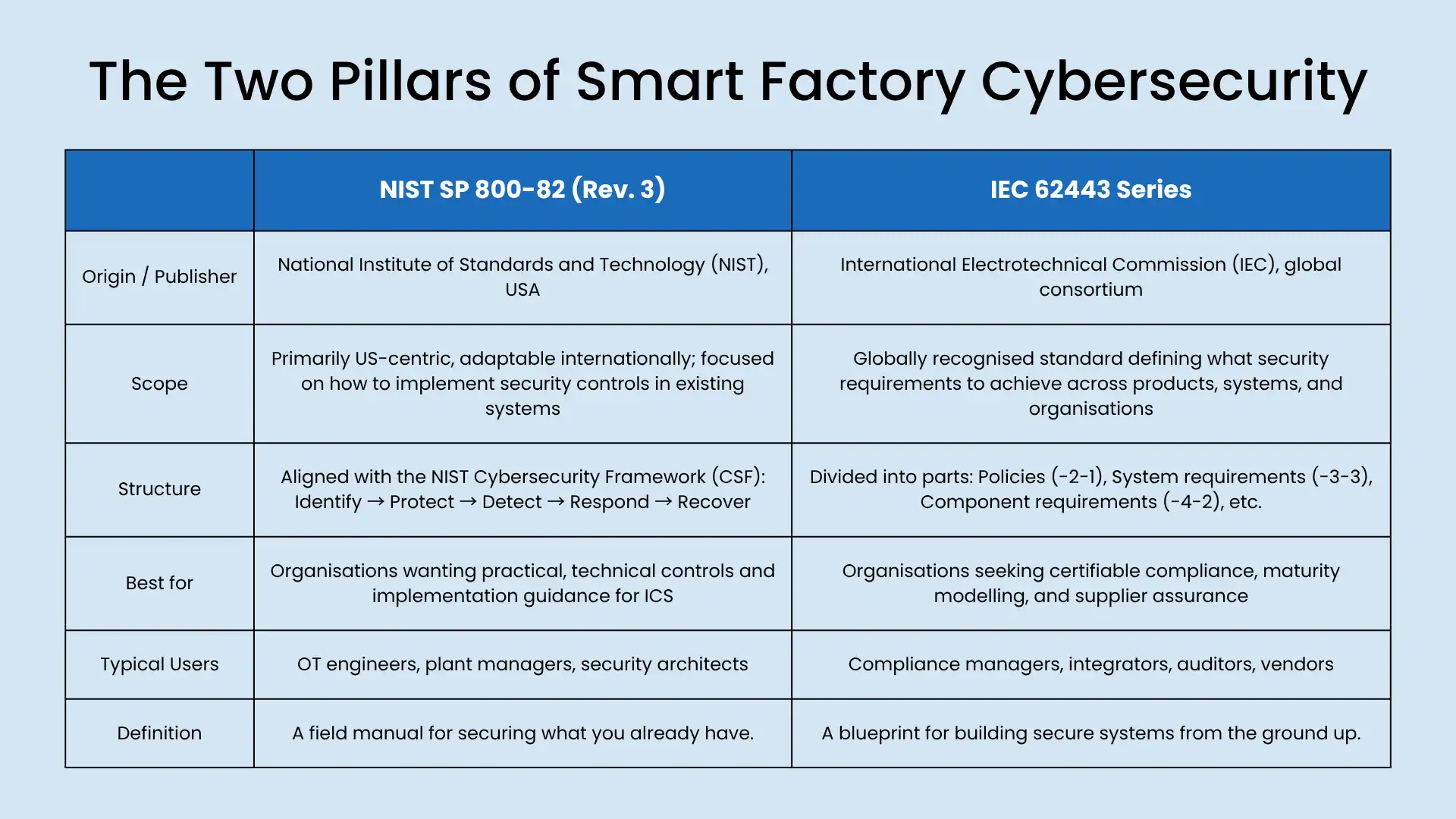
NIST SP 800-82 (Rev. 3): Practical guidance for Operational Technology (OT)—from architectures and typical ICS topologies to countermeasures that respect safety and real-time constraints. Think of it as a field manual to balancing security and uptime.
NIST Publications
IEC 62443: The global standard for industrial cybersecurity maturity. It’s modular: policies (62443-2-1), system security levels (-3-3), component requirements (-4-2). Use it to structure vendor requirements and internal audits.
Pro tip: Map your program to both use IEC 62443 for governance and supplier speak; use NIST 800-82 for engineering-level implementation.
“Cyber criminals are most often breaking in without breaking anything – capitalizing on identity gaps … Businesses need to shift away from an ad-hoc prevention mindset…”
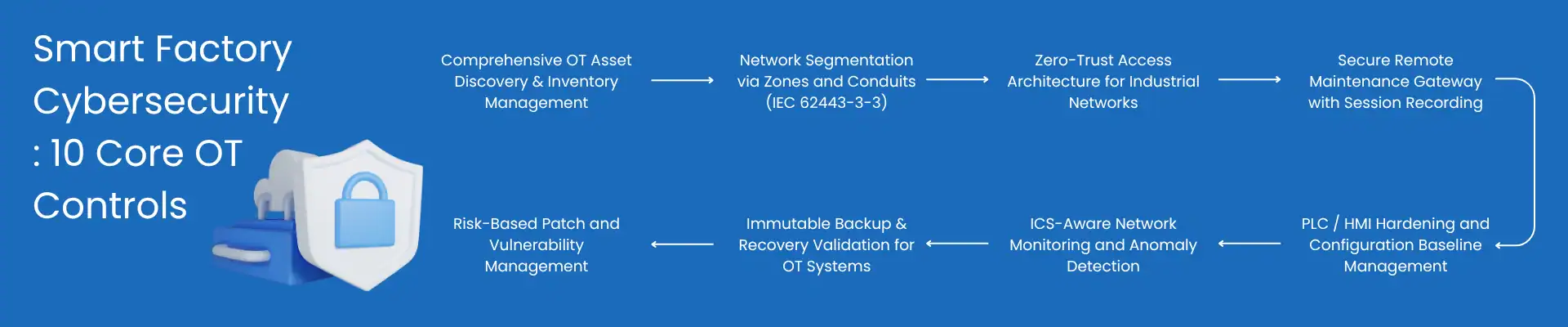
A pragmatic roadmap: 10 controls that move the needle
- Segment like you mean it (network segmentation & zones/conduits)
Implement OT zones (cells/lines, safety systems, historians) and controlled conduits to IT and cloud. Kill flat networks. Micro-segment high-value assets (HMI, PLCs, safety controllers). This is table-stakes in IEC 62443. - Identity at the edge (Zero Trust for OT)
Adopt device and user identity for everything crossing borders MFA for remote maintenance, ephemeral credentials, deny-by-default allowlists. NIST 800-82 supports identity-centric access even in latency-critical domains.
NIST Publications - Secure remote access (and audit it all)
Broker all vendor/engineer access through a jump server with session recording. For emergency break-glass, demand time-limited access and auto-revocation. - Harden the crown jewels (PLCs, HMIs, historians)
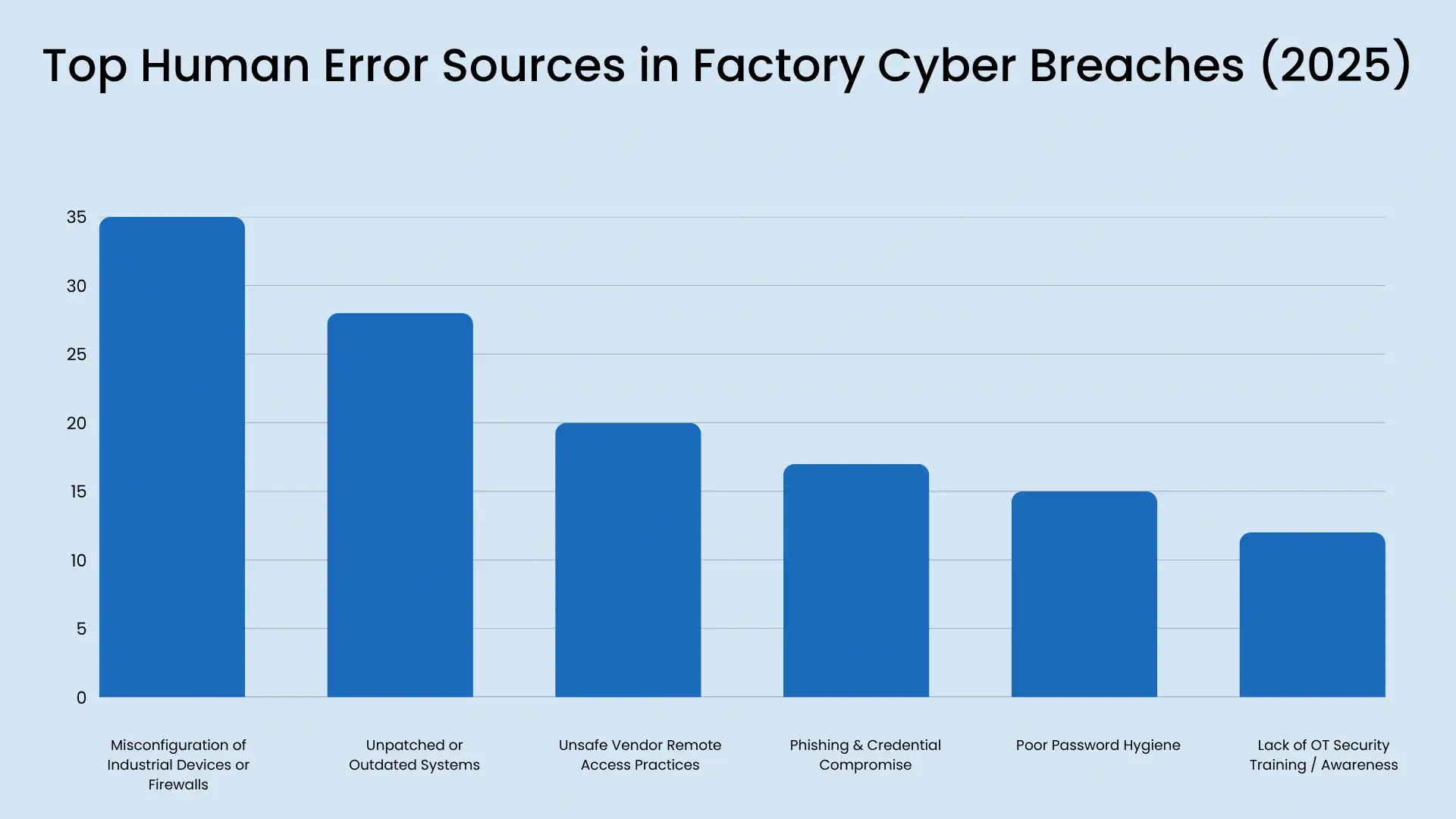
Disable unnecessary services, use unique creds (no password reuse), use signed firmware where supported, and version inventory. The majority of incidents start with out-of-date firmware + default creds. (Yes, still.) - OT-aware detection (ICS-friendly monitoring)
Passive network monitoring that is aware of industrial protocols (Modbus, Profinet, EtherNet/IP) to identify anomalies without interfering with determinism. Leverage baselining to alert on new talkers or function codes.
Number of infostealers delivered via phishing emails per week increases by 84%.
6. Immutable backups you can actually restore
Maintain offline/immutable backups of logic, recipes, and historian data; test time-to-restore per line. A backup you’ve never restored is a very expensive spreadsheet.
7. Patch carefully (risk-based maintenance)
Between “never patch” and “patch everything Friday,” choose risk-based: prioritise internet-facing assets, remote access, and known exploited vulns. Use maintenance windows aligned to takt times and batch cycles.
8. Supplier controls (contractual and technical)
Bake IEC 62443 terminology into contracts. Mandate SBOMs for connected components, vulnerability disclosure SLAs, and attested hardening guidelines. Suppliers are part of your factory treat them that way.
isa.org
9. Drill for the bad day (OT-specific incident response)
Exercise playbooks covering manual overrides, safe shutdown, and line-by-line recovery procedures. Coordinate IT/OT so containment won’t accidentally trigger safety or scrap WIP.
10. Measure it (from “nice slide” to KPI)
Measure MTTD/MTTR, percent lines with tested restore, percent vendor connections brokered, and security level targets (IEC 62443-3-3). What gets measured gets funded.
In 2024, the NCSC responded to 430 incidents, 347 involved data exfiltration, 20 involved ransomware
Architecture in a nutshell: from “flat and fragile” to “zoned and resilient”
- Level 0–1 devices (sensors/actuators/PLCs): No routable protocols if possible; implement vendor-recommended hardening.
- Level 2 (control/HMI): Micro-segment per cell/line; allowlist protocol/function codes.
- Level 3 (site ops/MES): Aggressive north-south filtering; one-way data diodes for historian/export where possible.
- DMZ: Only crossing to corporate IT/cloud. Jump hosts, inspection, patch/AV staging live here.
- Corporate IT / Cloud: Identity provider, SIEM/SOAR, data lakes. Make OT identities first-class citizens.
This mirrors NIST 800-82 guidance and the IEC 62443 zones/conduits model.
People and process: your unfair advantage
- Upskill maintenance techs as your first responders. They know what “normal” looks like at machine level.
- Make cyber part of Kaizen. When teams propose a throughput improvement, ask “what’s the security implication?”
- Tabletop twice a year. Include operations, safety, quality, and your top two vendors. You’ll find the gaps where process meets reality.
UK guidance now explicitly calls for executive ownership of cyber resilience. Translate that into a single accountable sponsor (Ops or Plant Director), a funded roadmap, and quarterly metrics.
Financial Times
“If your IT infrastructure was crippled tomorrow … could you run your payroll systems, keep your machinery working …? If the answer is no … act now.”
Compliance ≠ resilience (but it helps)
Employ IEC 62443 certification and NIST alignment as waypoints, not the destination. Audits show diligence; recovery time shows resilience. Regulatory drift is also worth monitoring: shorter reporting windows and supply-chain demands are coming into view for growing numbers of manufacturers.
Final word
Smart factories win on speed, quality, and flexibility but only if they can withstand modern cyber pressure. The data says attacks are more frequent and more sophisticated; the standards tell you how to build a defence that respects uptime and safety. Put them together, measure relentlessly, and make security a competitive advantage.
Explore more related content
Strategic Global Sourcing: How Companies Move from Cost Saving to Competitive Advantage
Strategic Global Sourcing: How Companies Move from Cost Saving to Competitive AdvantageSupply chain disruptions now...
Critical Minerals, Critical Thinking: Building Resilient Electronics Supply Chains
Critical Minerals, Critical Thinking: Building Resilient Electronics Supply ChainsThe global economy is expected to...
Digital Product Passports for Small Appliances & Air Purifiers
Digital Product Passports for Small Appliances & Air Purifiers: A 2025–2027 Manufacturer Playbook From the Oxera...